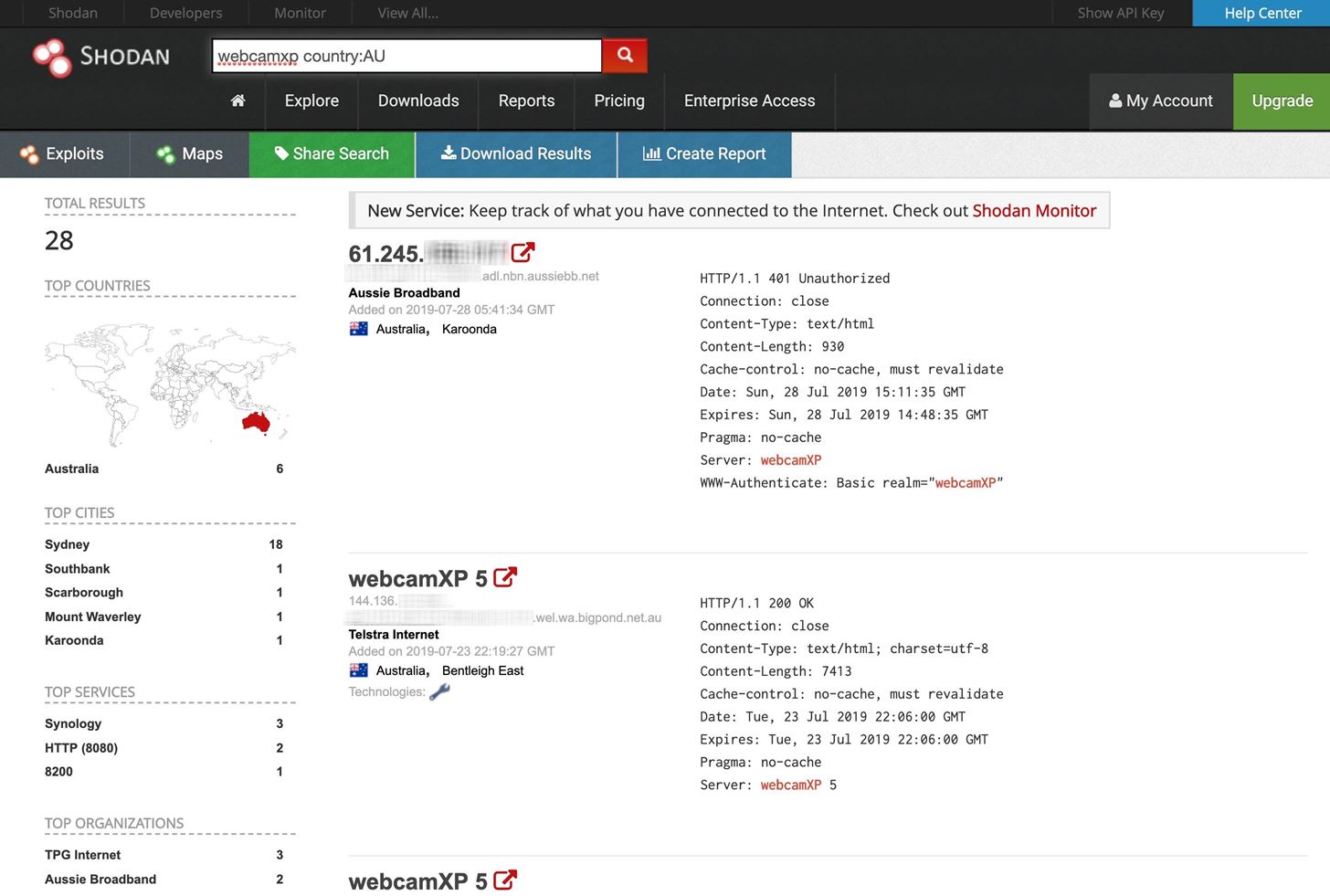
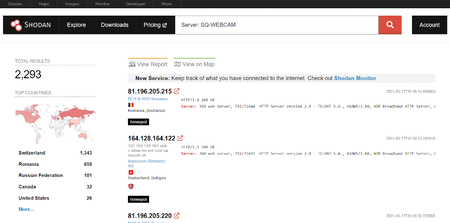
PenTest Edition: Using Shodan to Locate Internet-Connected Devices (Webcams, Servers, Routers, and More) – The Cybersecurity Man

PenTest Edition: Using Shodan to Locate Internet-Connected Devices (Webcams, Servers, Routers, and More) – The Cybersecurity Man

Shodan, cos'è e come permette di scovare webcam, router, NAS e altri dispositivi remoti | IlSoftware.it

OSINT with Shodan: Information gathering on the servers of your organization | by Melusi shoko | System Weakness
The Dark Side Of The Internet: A Search Engine That Finds Unsecured Routers, Servers & A Whole Lot More

Shodan on Twitter: "We've updated the design for Shodan Images and improved the performance (requires a membership): https://t.co/IWbKMi6Pgr https://t.co/7brDaoh5zo" / Twitter